Background
The purpose of this internal research and development project was to learn more about cybersecurity testing of 5G devices by discovering how cyberattacks can be executed on them and establishing repeatable processes for assessing cyber vulnerabilities in 5G-connected devices. For this purpose, the team sought to adapt existing 4G LTE testing methodologies to newer 5G devices, especially the establishment of a man-in-the-middle (MitM), which represents a worst-case attack scenario in which full control can be exerted over all communications between endpoints.
Approach
The approach for 5G vulnerability evaluation requires the ability to intercept communications between the two target 5G devices. First, both the access point and devices needed to be set up and tested for basic connectivity and function. This included construction of hardware and installation of software necessary for the devices to connect through the base station. The base station uses a software-defined radio (SDR) with specialized software to control the radio frequency (RF) signals of the base station. The preliminary test devices consist of a microcomputer with a 5G modem card and the appropriate antennas. This forms a flexible platform that allows customized applications to communicate over 5G, simplifying test development. Following this step, the team planned to verify the connection by observing the communications between the devices via an open-source network protocol analyzer. Once a connection between two 5G devices was established and verified, the team would run basic applications over this connection and use the system to experiment with adapting 4G testing methodologies to 5G, developing a framework and platform which could be used to execute these capabilities for clients.
Accomplishments
The team was able to establish a 5G base station which could pose as the MitM and allow for implementation of various vulnerability testing capabilities. The core hardware was also assembled for driving the 5G modems which served as test modules for sending and receiving arbitrary signals over the 5G network. For future devices under test, these hardware and software components can be used in an RF chamber to intercept and alter communications on the fly.

Figure 1: Hardware assembly for the 5G devices.
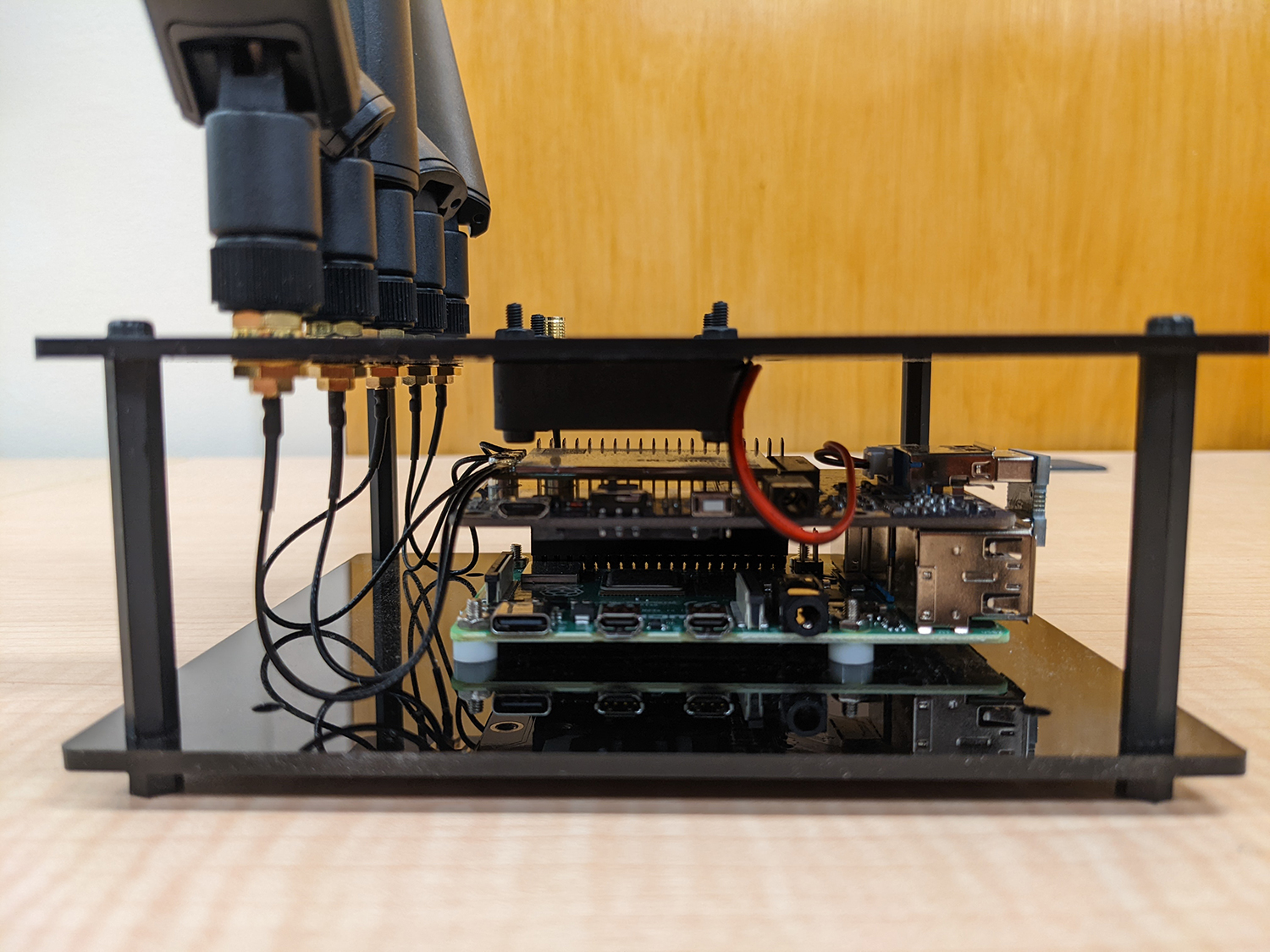
Figure 2: Hardware assembly for the 5G devices.
