Background
Since the early 1990’s, commercial vehicles have suffered from repeated vulnerability exploitations that resulted in a need for improved automotive cybersecurity. This paper describes the strategies and challenges involved in securing vehicle networks through the implementation of an automotive Zero Trust Architecture (ZTA). Zero Trust, originally an IT principle of “never trust, always verify”, is the concept that a network must never assume assets can be trusted regardless of their ownership or location within the network. This research focused on drastically improving security of the cyber physical vehicle network with minimal performance impact, measured as timing, bandwidth, and processing power. Impacts to safety and cost were also considered.
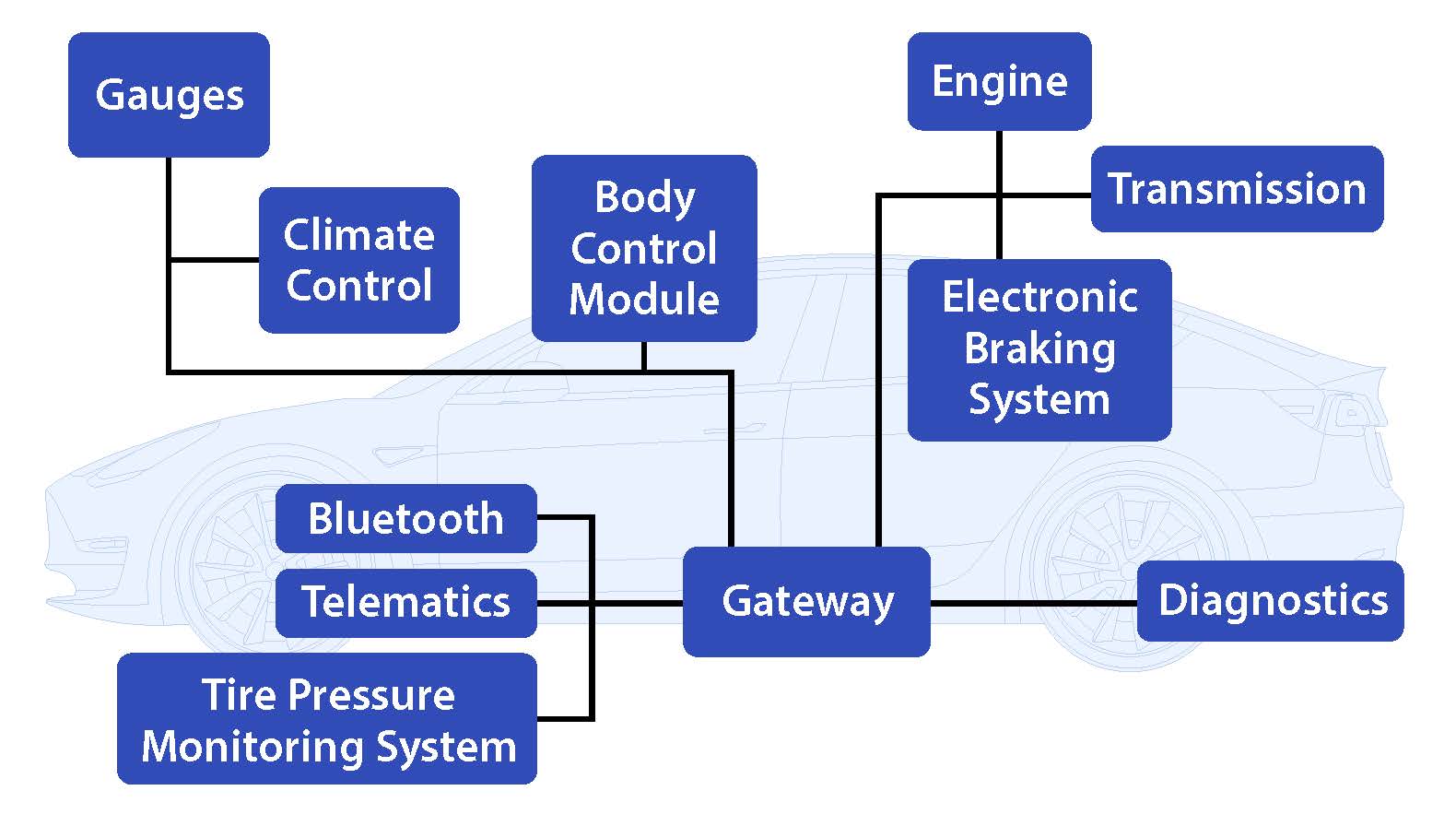
Figure 1: Traditional Vehicle Architecture
Approach
The automotive ZTA was tested using a software-in-the-loop vehicle simulation paired with resource constrained hardware that closely emulated a production vehicle network. This ZTA solution leverages the best cybersecurity practices from the IT industry and preexisting vehicle architecture components. For example, the vehicle gateway electronic control unit (ECU) is utilized to enforce cyber policy, monitor the network, distribute keys, and implement network segmentation. Other applied security solutions include Secure Onboard Communication (SecOC) for authentication and verification of network communication and secure boot to ensure the system is running authentic software. Implementing these elements and the other security controls is complicated by cost, resource constraints, and the complexity of building and maintaining vehicles. This research successfully demonstrates that using Zero Trust principles in an on-vehicle network greatly improves the cybersecurity posture with manageable impact to system performance, cost, and deployment.
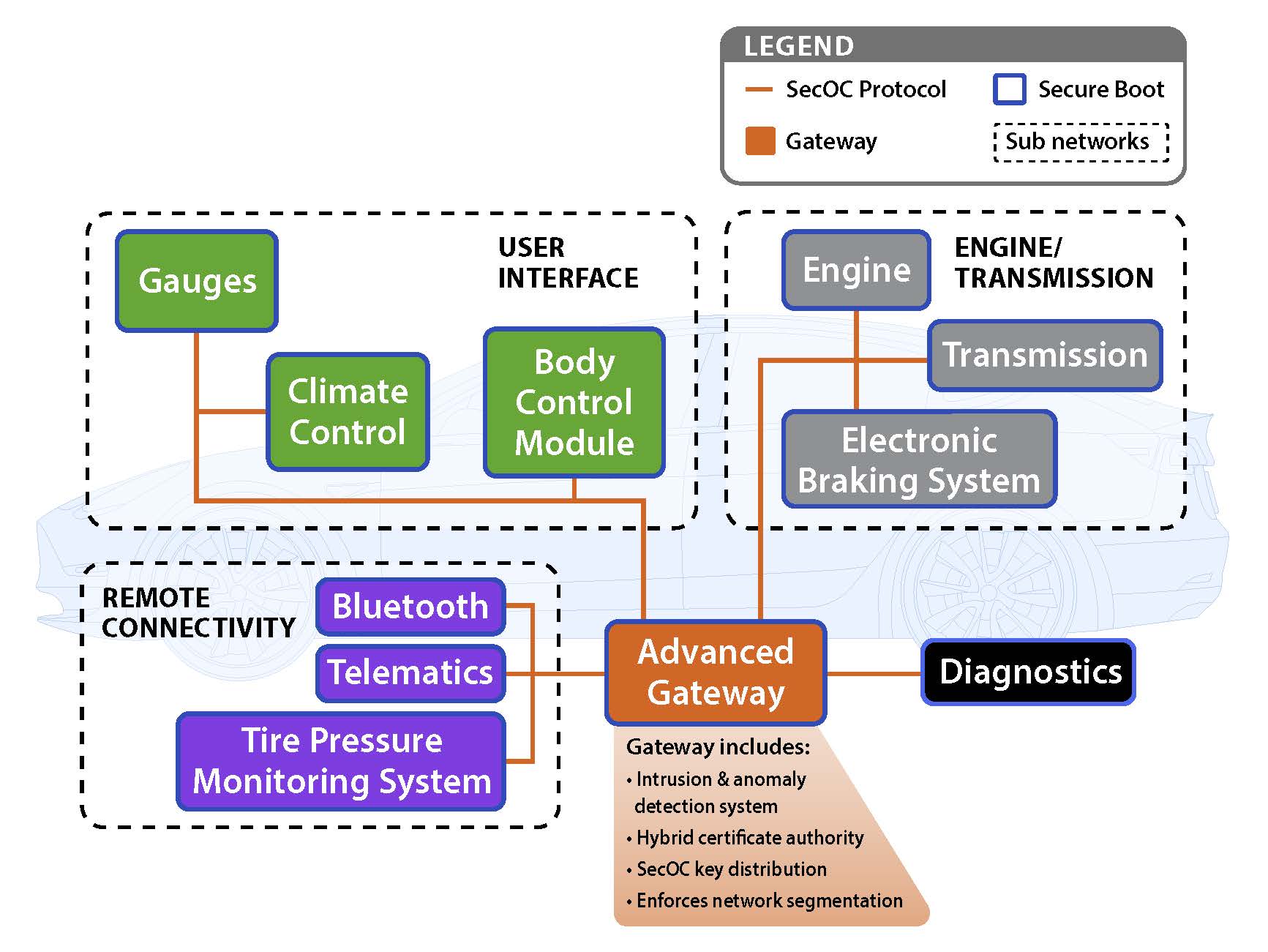
Figure 2: Zero Trust Vehicle Architecture
Accomplishments
Research is currently active. However, success thus far has included implementation of the Secure Onboard Communication Protocol, Secure Boot, ECU authentication, key creation, and distribution, as well as a monitoring system. The Zero Trust Architecture concept has been successfully demonstrated through a software-in-the-loop vehicle simulation utilizing Raspberry Pi’s to model ECUs as shown in Figure 3. Moving forward, the simulation will be adapted to a higher fidelity model that will include hardware more similar to that seen within a fielded vehicle.
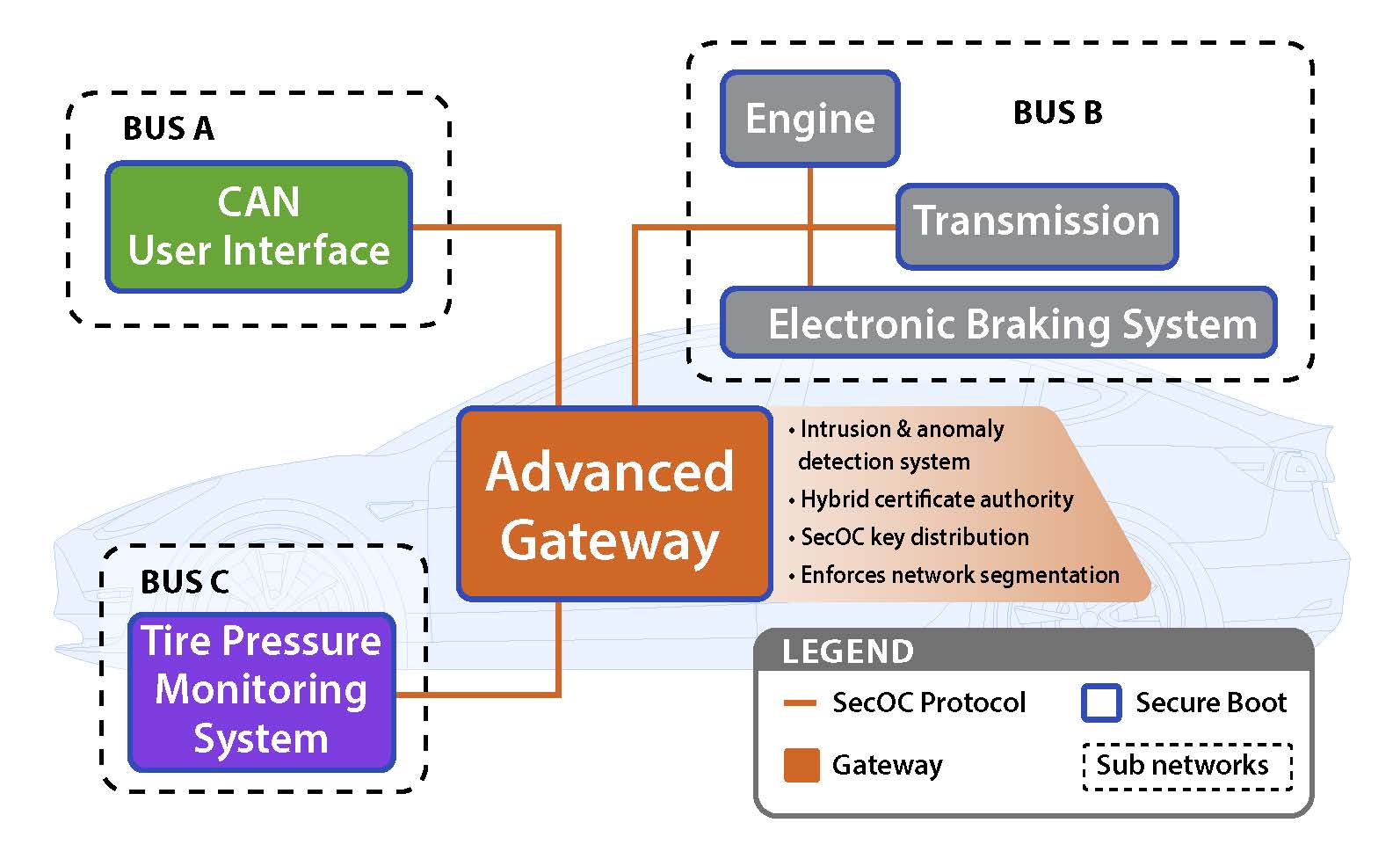
Figure 3: IR&D Zero Trust Vehicle Architecture Simulation
