Background
The Controller Area Network (CAN) is a highly reliable serial bus communication system originally developed for in-vehicle networks, allowing for various electronic control units (ECUs) to communicate. However, the CAN as a standalone protocol lacks sufficient security practices enabling any ECU on the network to transmit any CAN packet, or message, to any other ECU. To protect the network from unintended or malicious CAN packets, also known as anomalous messages, research has been done to digitally fingerprint ECUs, or identify unique patterns between different ECU’s CAN packets by utilizing physical characteristics, such as voltage levels or timing. However, past efforts in this space were often hard to integrate into existing CAN buses due to the need for additional hardware and required re-configuration of algorithms for each network the system was introduced to.
Approach
In response, this effort aimed to identify a new metric that could accurately identify when anomalous messages were present on the network, while also mitigating the issues seen in previous implementations. An embedded system was chosen to calculate the real-time measurements as it allows for easy integration into ECUs since they are embedded systems themselves. This effort was done by investigating different timing metrics with multiple commercial vehicles and an automotive testbench setup. Measurements were then provided to statistical models to determine if ECUs could be grouped by unique timings.

Figure 1: Points of the test network.
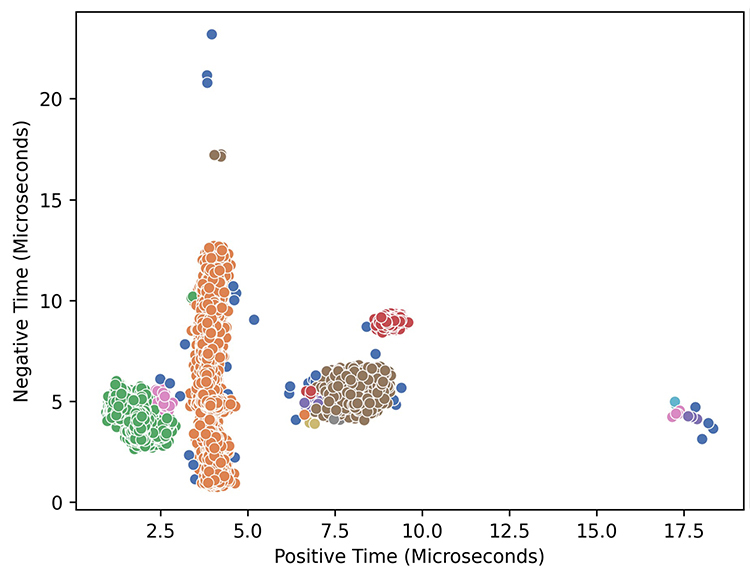
Figure 2. Results of the clustering algorithm.
Accomplishments
It was found that characterizing messages by the time passed over a single bit in a frame required no algorithm re-configuration when introduced to new networks. For final testing, two vehicles were used to test this novel implementation: one traditional internal combustion engine (ICE) gas vehicle and one electric vehicle (EV). In testing, the true positive rate (the rate that an anomalous packet was marked as anomalous) was 99.77% and the false positive rate (the rate that a non-anomalous packet was marked as anomalous) was 0.11% for CAN identifications (IDs) that could be characterized (IDs that were seen during training that data could be captured for). With a false positive rate less than a fraction of a percentage, this novel implementation is capable of accurately identifying anomalous messages, introducing a new possible defense solution to any system that utilizes a CAN bus.

Figure 3: True positive vs false negative results of attack test

Figure 4: True negative vs false positive results of attack test
