Background
This internal research and development (IR&D) explored methods to apply security capabilities to operational Robotics Operating System (ROS) 2 environments. These security capabilities included fuzzing techniques for vulnerability detection and adapting existing ROS 2 processes to work with Secure Robotics Operating System (SROS2). The new security features in SROS2 introduce complexity, with much of the ROS 2 tooling proving to be difficult and unintuitive to use when security is enabled. Additionally, vulnerability detection tools that had worked with unsecured ROS 2 environments had not been tested with SROS2.
Approach
This IR&D effort included two parallel phases: 1) investigating methods for identifying SROS2 system security vulnerabilities, and 2) adapting ROS 2 command line tools to SROS2. During phase 1 of the IR effort, a lack of version compatibility between the latest stable ROS 2 distribution and the ROS fuzzing tools originally intended to be explored during this IR&D was discovered. Following this, an adjusted approach utilizing Wireshark and Python fuzzing scripts was taken for vulnerability discovery, leveraging methods used in SwRI’s previous penetration work. For phase 2 of the effort, specific SROS2 tool adaptations for introspection and configuration capabilities were identified and tested, specifically targeting the “ros2 node info” tool and enclave specification.
Accomplishments
Fuzzing techniques were effectively implemented in this project, revealing valuable insights into the security robustness of an SROS2 environment. The findings emphasize the importance of continued exploration and application of vulnerability discovery techniques, particularly in unsecured ROS 2 environments where vulnerabilities may be more readily exposed. Efforts to adapt the ROS 2 command line tools to provide additional security introspection and configuration were successful. Continuation of this work may include submitting these changes as pull requests to the open-source ROS 2 repository, or otherwise taking the efforts performed in this work and incorporating them into ongoing or future projects.
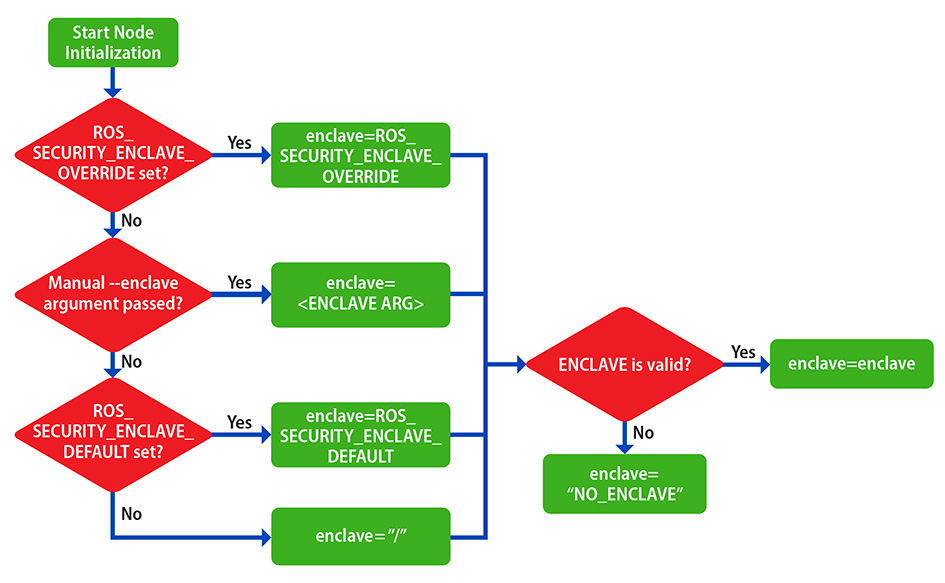
Figure 1: Enclave Flowchart.
