Background
This research explored the applicability of blockchain technology to Vehicle-to-Vehicle (V2V) and Vehicle-to-Everything (V2X) platforms to improve the security and reliability of corresponding networks. As connected vehicles become part of a critical infrastructure, the damage a potential attack would cause will also increase. This potential is twofold. First, an attack may attempt to take remote control of one or more vehicles. Second, an attack may target personal information onboard a vehicle. Recalls due to security vulnerabilities in connected vehicles have already occurred. Consequently, security in connected vehicle platforms has become a concern of both end users and manufacturers.
Approach
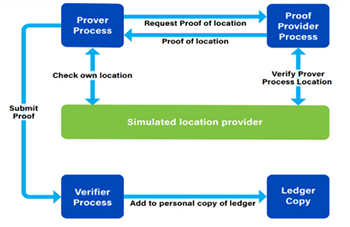
Figure 1: Node Interaction Diagram.
This research sought to implement a blockchain utilizing and building on an existing proof of location scheme. This scheme contains three processes working in tandem. Each process exists on all physical nodes on the blockchain network. The interaction of these processes is shown in Figure 1.This research used location as proof, rather than proof of location layered on a proof of stake mechanism. No cryptocurrency was used for this implementation since compensation for communication and computation was deemed unnecessary as all vehicles involved benefit directly from the exchange of information.
Accomplishments
The only means of attack that this research deemed effective was a 51% attack. This attack is a known weakness of blockchain. Existing networks focus on how to prevent this method from being practicable rather than extant. As the size of the network grows, the difficulty of the attack increases. Other attacks implemented were rebuffed by the plausibility check. In this research, the location assessment mechanism was assumed to be correct within a small margin of error. Such a scheme is another area of ongoing research. Voting mechanisms, including the one created in this research, may serve as a redundant check to accommodate errors in location assessment.

